|
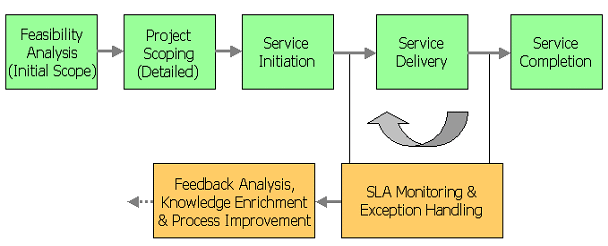
BizPro’s goal is to deliver the highest possible quality in every engagement. One cannot hope for quality to come by chance and must ensure it proactively. Hence, BizPro follows a systematic process in its outsourcing engagements (see diagram below) and incorporates adequate quality checks at all key milestones.
In most engagements, BizPro assumes end-to-end process responsibility. In the early stages this involves working closely with the customer to identify the key performance indicators (KPIs) for the intended project, collects detailed requirements and conducts a feasibility analysis. A high-level project scope is often used in this phase. If the project is found viable, then a detailed scoping exercise is undertaken. During the service initiation phase, these details are then used to select delivery resources and to create service level agreements (SLAs) between all relevant parties. A set of relevant performance metrics forms the basis of the SLAs. A constant monitoring loop over the service delivery sub-process is used to manage SLAs as well as to capture and handle delivery related exception. Pertinent information is continually extracted from the delivery monitoring sub-process in order to gain further insight into the workings of outsourcing process, which can then be utilized to better the process itself.
|